An Introduction to Secret Shared Validators (SSV) for Ethereum 2.0
Secret Shared Validators (SSV) is a R&D effort to improve on Ethereum's validator infrastructure for Eth 2. Learn more about the latest tech.
Secret Shared Validators (SSV) is a joint R&D project with the Ethereum Foundation (EF), the first secure and robust way to split Eth2 validator keys between non-trusting operators which can transform staking services, pool performance, and security.

Staking on Ethereum is somewhat unique as every validator requires 32 ETH and has to run a dedicated software 24/7. Staking can carry significant rewards, alongside penalties and even in the most severe cases, slashing (the highest penalty + being kicked out of the protocol).
Different staking setups have emerged in recent months, from DIY configurations all the way to staking pools. What hasn’t changed is the actual infrastructure on which these different services are built. Due to the stringent rules that the Eth2 slashing protocol defines, all staking configurations must run a validator using a single validator client.
Running a single validator on multiple validator clients can have catastrophic results as we saw with the mass slashing events that stkr and staked.us suffered, both of which tried to optimize their uptime and performance by running multiple validator instances, resulting in those validators being slashed.
The constraint of running just 1 validator instance also influences staking pool designs to be more centralized and less secure. The SSV project is developing a technology that enables the splitting of an Eth2 validator key between several operators in a trustless, decentralized and secure way. This reduces the reliance on any single point of failure that might affect a stakers validator performance and ETH rewards and increases network security by focusing on decentralization across the entire network.
To deliver SSV technology, there are 3 main components to consider: Key Splitting, a Consensus Layer, and a Communication Network.
All Eth2 validator keys are BLS12–381, a unique cryptographic signature based on bi-linear pairings. Two of its prominent properties are the ability to aggregate signatures/public keys and that a signature on the same blob of data is always the same (deterministic), unlike other cryptographic signature schemes.
The first step in any SSV setup is to split an existing key between the network operators (using Shamir Secret Sharing for example) or jointly generate a secret key via Distributed Key Generation (DKG) schemes.
The end result is a set of M operators each having: unique share S_i of the secret key (SK) and the public key (PK) that matches (PK=SK*g, for some generator). Key splitting is built in a way that enables reconstructing a signature made by SK if m-of-n operators sign it. In layman’s terms, this mechanism ensures that the key can be divided and distributed across network participants and a pre-defined number of participants are needed in order to recreate the key for signing.
The beacon chain randomly assigns duties to each validator with a public key PK. A duty is executed by signing a specific data structure (that changes if it’s an attestation/aggregation or proposal) in the correct way. For a group of M operators agreeing on what to sign is crucial, this is a classic BFT problem solvable via consensus.
Research done by Dankrad, Carl, and Aditya of the Ethereum Foundation marked Istanbul BFT (IBFT) as a good candidate for the consensus layer as it’s a simple and robust protocol, suitable for the SSV use case.
IBFT is an O(n²), 3 phase round BFT. A leader is deterministically selected every round, a valid leader broadcasts a PRE-PREPARE message to all other parties containing a proposed data to sign. Upon receiving a valid pre-prepare message, all parties broadcast a PREPARE message. Upon receiving a quorum of valid PREPARE messages, all parties broadcast a COMMIT message. Upon receiving a quorum of COMMIT messages the round concludes and is finalized. iBFT can tolerate up to f faulty operators out of n, n >= 3f+1.
Key-Splitting + IBFT are the foundation of every SSV node, first nodes decide on what to sign, after which they sign the data and individually reconstruct it once n-of-m signatures are broadcasted.
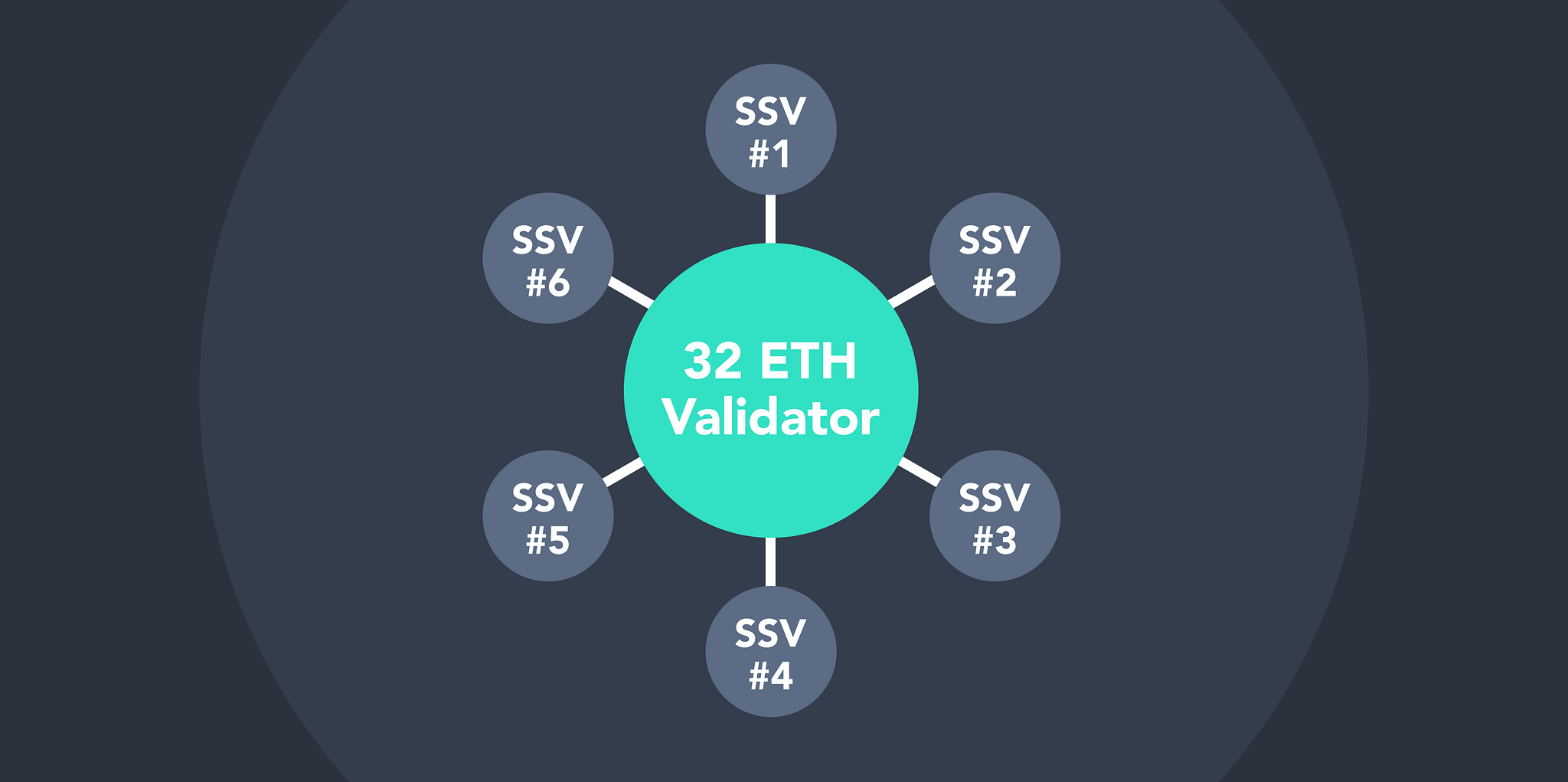
To connect Key Sharing and SSV nodes into a giant mesh where validators can get generated on the fly between dynamic sets of operators we need a network (a communication network) built with those abilities in mind.
Each validator created has its own set of operators, each operator can be assigned to several validators. A many to many structure. The goal of a network is to facilitate that flexibility alongside network exploration, discovery, and more.
SSV, at its heart, is a way to decentralize risk and reduce failures by making individual SSV nodes become a robust network that can outperform any individual staking service in security, robustness, and uptime. Through developing this technology we can improve ETH rewards for stakers, increase network decentralization, and also significantly reduce staking risks.