SSV Network’s New Distributed Key Generation Tool
Explore SSV DAO's introduction of DKG, bolstering protocol security with a toolkit for trustless, non-custodial staking services.

The SSV DAO is thrilled to share the new Distributed Key Generation (DKG) tool, a… key milestone in enhancing the security and trustlessness of the ssv.network protocol. DKG is a different way to enable distributed node operation and a meaningful tool for building non-custodial staking services on the SSV Network.
This blog post will outline DKG, the components of the ssv-dkg tool, how the tool works, and why it’s crucial to have the option to use it.
TL;DR
In ssv.network DKG is a powerful tool that improves the security of validator private keys and opens up a new avenue for trustless and non-custodial staking services to build on the protocol. Using DKG, the validator private key never has to exist, meaning validator duties are conducted without a staking service, solo-staker, or squad-staking setup ever holding the key.
To understand why DKG is essential, one has to know why keyshares are essential. In a nutshell, keyshares are a critical component of distributed validator technology (DVT). They enable clusters of node operators (a.k.a. operators) to run validators in a distributed manner. Each operator in a cluster holds a keyshare; when signing duties are required from the Beacon chain, keyshares are used collectively to sign duties on behalf of the validator.
Each operator in a cluster can have varying components, i.e., EL/CL clients, locations, or even infrastructural setup (hardware/cloud). By using keyshares, diverse node operators can provide much higher levels of security, fault tolerance, and decentralization than the standard validator (non-DVT) setup.
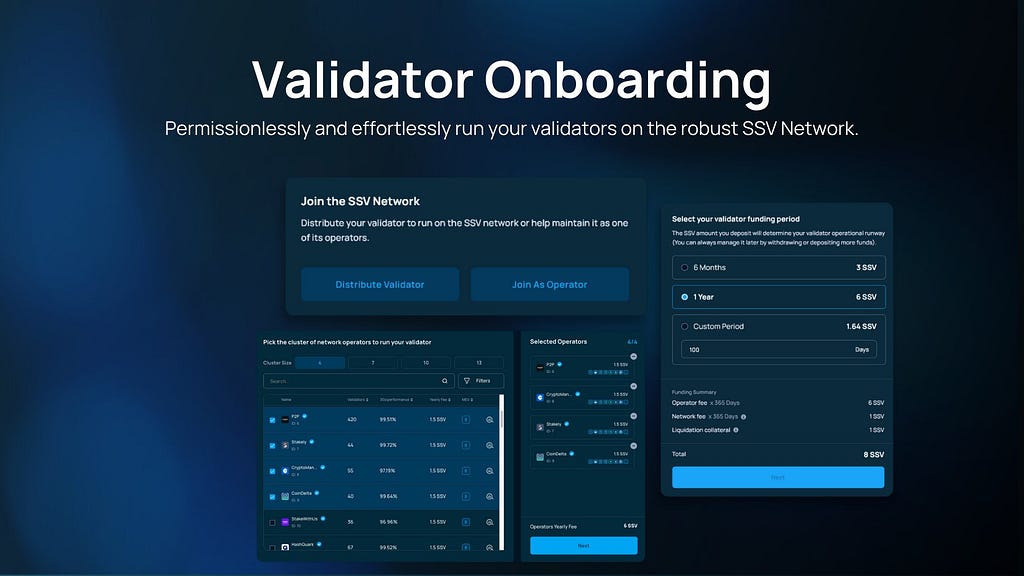
Validators registered on ssv.network can choose which node operators to delegate their keyshares to (they can also be customized with zero-coordination via a simple, smart contract transaction). When deciding which operators to delegate keyshares to, users can choose whether to do it via DKG or Key-splitting.
Before DKG, a key-splitting tool takes the validator’s private key as input splits, encrypts, and distributes the keyshare between chosen operators. This allows stakers with existing keys to easily onboard and distribute their validator on the network.
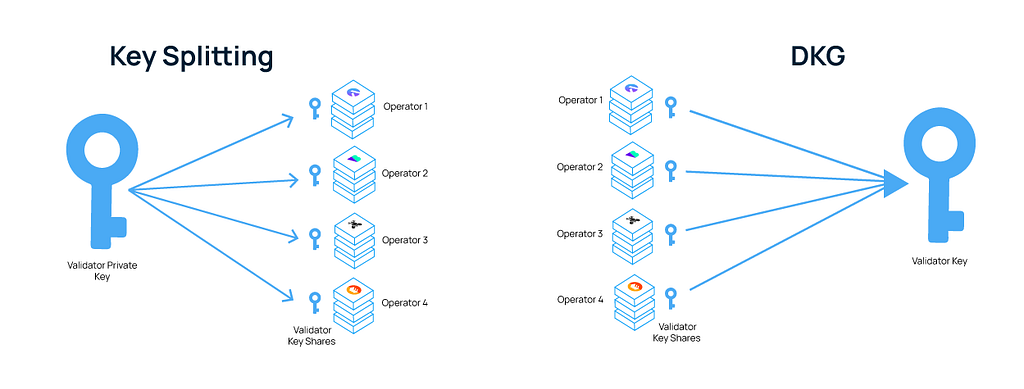
On the other hand, DKG is used for instances where stakers don’t want the private key to exist at all, i.e., non-custodial staking services, institutions, and at-home stakers using DVT. As the names suggest, it’s genuinely splitting vs. generating. Since the ssv.network is an agnostic protocol, users and builders should be able to choose which option best suits their needs.
To draw a metaphor, you can think of a validator private key as a treasure map. Key-splitting would be having the map in the first place and tearing it into as many separate pieces for each operator in a cluster.
While DKG would be having the operators draw their own pieces. These pieces are the keyshares mentioned above. The process to obtain them is different, but the end result is the same: when they all come together, the map can be complete. The big difference is that the whole map could have been seen and memorized with key-splitting.
With DKG, the whole map is never known, no one has to trust each other, and at no point is anyone in possession of the whole map. This translates to:
Improved security — DKGs enable a group of parties to collectively generate a secret and public key pair in a distributed manner, protecting it from being exposed, even if a certain number of parties are compromised.
No key management needed — Companies/stakers don’t have to spend time, money, and effort to manage keys to prevent security leaks.
Increased trustlessness — Stakers can use a staking service or pool, knowing they don’t hold validator keys. For some use cases, it’s better than being non-custodial. This also means fewer trust assumptions exist between services and node operators.
For staking services building on ssv.network, it means less key management — they don’t have to hold any validator private key at all. When staking pools reach a threshold of 32 ETH, operators are chosen and can easily create the new key without needing to store it. The same applies to solo stakers using the protocol now since the Permissionless launch.
Solo-stakers can use their existing infra to become one of the node operators in their own cluster, simultaneously opening up their services to other validators so they can earn SSV protocol rewards.
As part of Lido’s new SimpleDVT and community staking module (CSM), there is potential for assigning operators using DKG. In fact, by using DVT, Lido will be able to expand its node operator set permissionlessly in the future. Using DV tech can also reduce the bond requirements by splitting it between the participants in a cluster, making staking more accessible.
The ssv-dkg tool enables operators to participate in ceremonies to generate distributed validator keys for Ethereum stakers. The tool mitigates centralization risks and malicious actors through a robust signature verification mechanism. The tool was developed using state-of-the-art, battle-tested libraries.
The ssv-dkg tool is separate from the ssv-node and could run on a different machine. The two are heavily correlated, as the keyshare generated by the ssv-dkg tool is ultimately used by the Node to manage the related validator.
Simple discovery — The DKG tool was developed to be user-friendly and highly secure. The key differentiating factor to other DKG tools lies in how participants for the ceremony are found. By using a P2P network and zero coordination, all operators need to do is share their endpoint in the metadata section of their profile to enable discovery.
Customization — A unique benefit and powerful feature of ssv-dkg is its flexibility and customizability. When a cluster encounters a buggy, under performing, or malicious operator, it can be switched out with others in the network. By resharing, operators can recreate a DKG ceremony with a new operator set with a simple transaction. This allows stakers to switch out operators with the click of a button.
Exit when you want — Validators who want to exit can do so by having the threshold (3/4, 5/7, etc.) of operators sign the exit message to leave the network. Alternatively, validators will be able to use a pre-signed message that requires no operators to sign (not yet implemented at the time of writing).
For the DKG protocol to execute successfully:
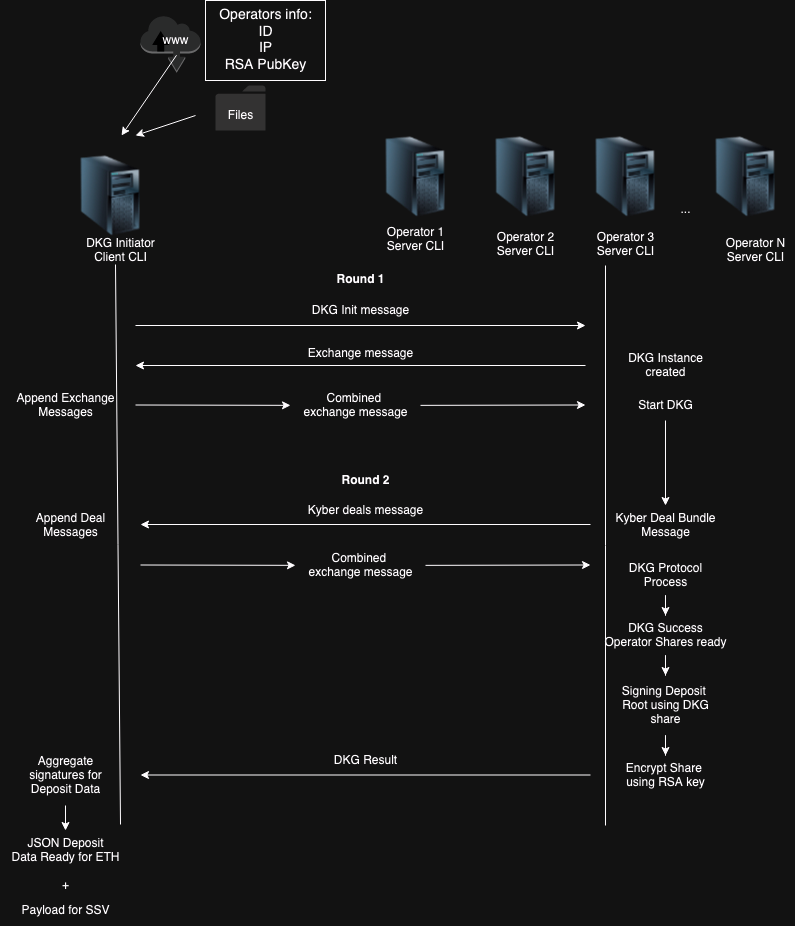
To read the entire flow, see the SSV DKG docs.
SSV is a permissionless infrastructure for stakers, builders, and node operators. Different mediums are available to support each of these tenants. When staking directly with SSV, users can use the web app and Docker. Builders can build it straight from the source in their applications.
In a few easy steps, stakers can be set up and start staking with DVT with no existing key required. SlowMist is currently auditing the tool. Following the feedback implementation and a second round of testing, the tool will be ready for mainnet!
The first step is to choose DKG-enabled node operators — as shown in the screenshot above. Then select DKG as the method you’d like to use to generate keyshares. Launching the tool as a Docker image is advised as it is the most convenient way and only requires having Docker installed. The team builds a Docker image with every release of the tool.
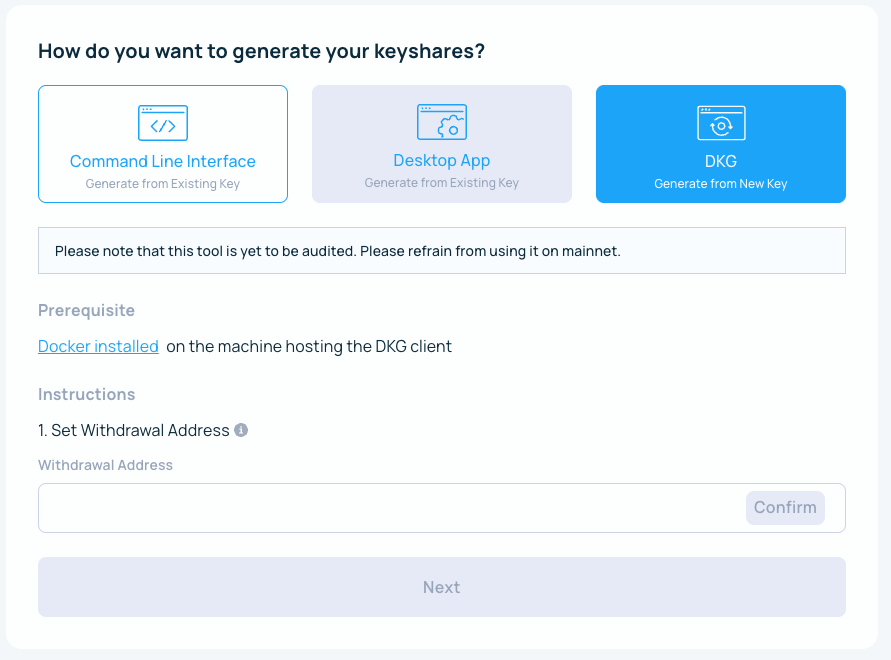
Set a withdrawal address and initiate the ceremony with the command provided in the UI.
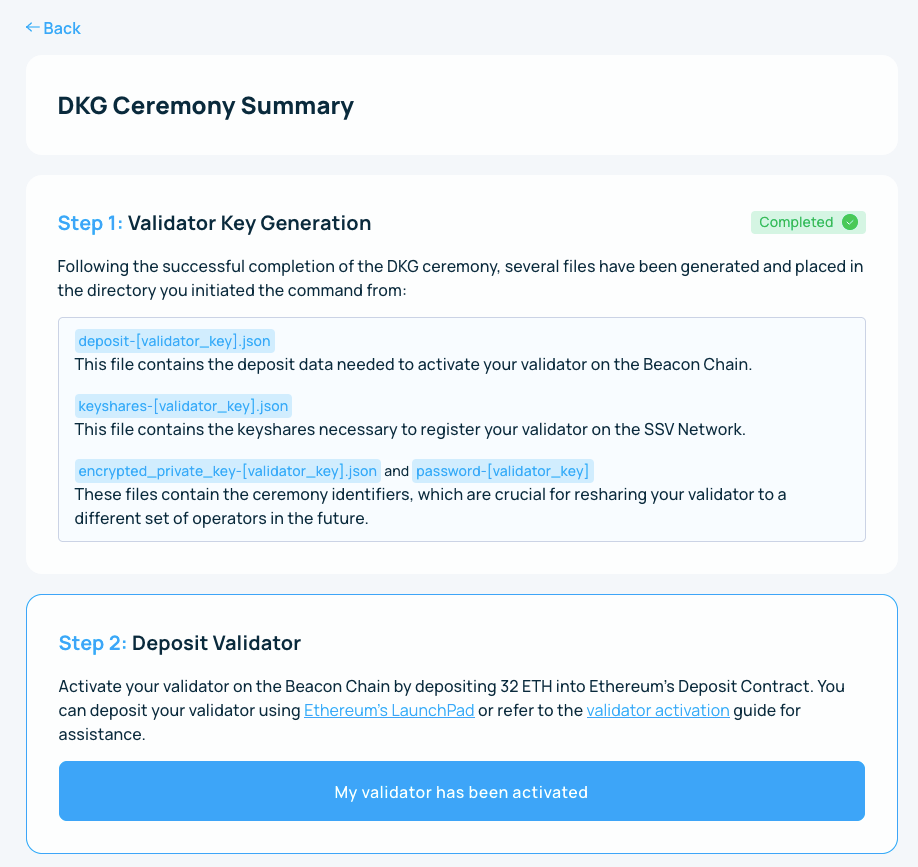
Deposit 32 into the Ethereum Deposit Contract.
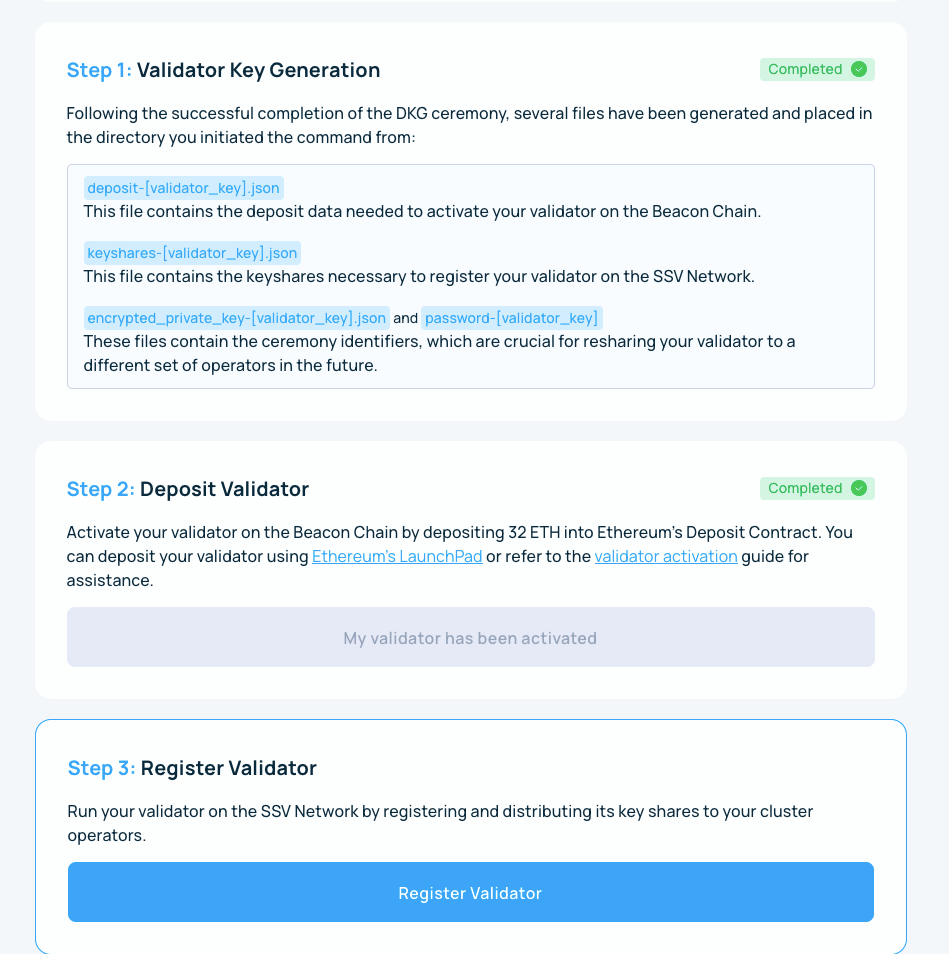
The last step is to upload the generated keyshares.json, and Bob’s your uncle! Your distributed validator is registered to the network and ready to go.
Documentation & Guides
For those eager to dive in, check out the comprehensive documentation and guides:
The SSV DKG tool represents a leap in the realm of cryptographic security, and the Core team is excited about its potential for enhancing the safety and trustlessness of the SSV protocol for developers and stakers alike.
Website | Builders Hub | Network Hub | Discord | Dev Center | Documentation | GitHub